When CRC16 is not Enough
24-11-2025
There are a ton of possible checksum implementations. What’s worse is there can also be custom polynomials, and non-standard checksums. Thankfully, most of us software engineers are lazy, so we just use an existing implementation.
Documentation? Maybe if I feel like it. Now, where did I write that initial value…
Introduction
It connects on my device!
If you work with embedded devices long enough, this story starts to sound familiar:
The documentation says “CRC16 checksum”, maybe even lists a polynomial if you’re lucky, but that’s it. No details about byte order, reflection, initial value, or final XOR. You implement what seems reasonable, but the firmware keeps rejecting your packets.
The CRC Confusion Problem
Cyclic Redundancy Check is not a single algorithm; it has many variants, each defined by multiple parameters:
- Polynomial: the core math of the CRC
- Initial value: starting point of the calculation
- Reflected input/output: bit order reversal
- Final XOR value: optional final transformation
- Byte order: least or most significant byte first
Even two CRC16 implementations that use the same polynomial can produce different results if any of these parameters differ.
CRC parameters all affect checksum results
A Simple Trick: Let the Data Tell You
Instead of guessing variables, why not use a real packet with an actual CRC to identify the correct variant?
- Capture a known packet with both the raw data and the actual CRC.
- Go to crccalc.com.
- Paste your data and try the different CRC16 variants.
- Compare the calculated checksum with the expected value until it matches.
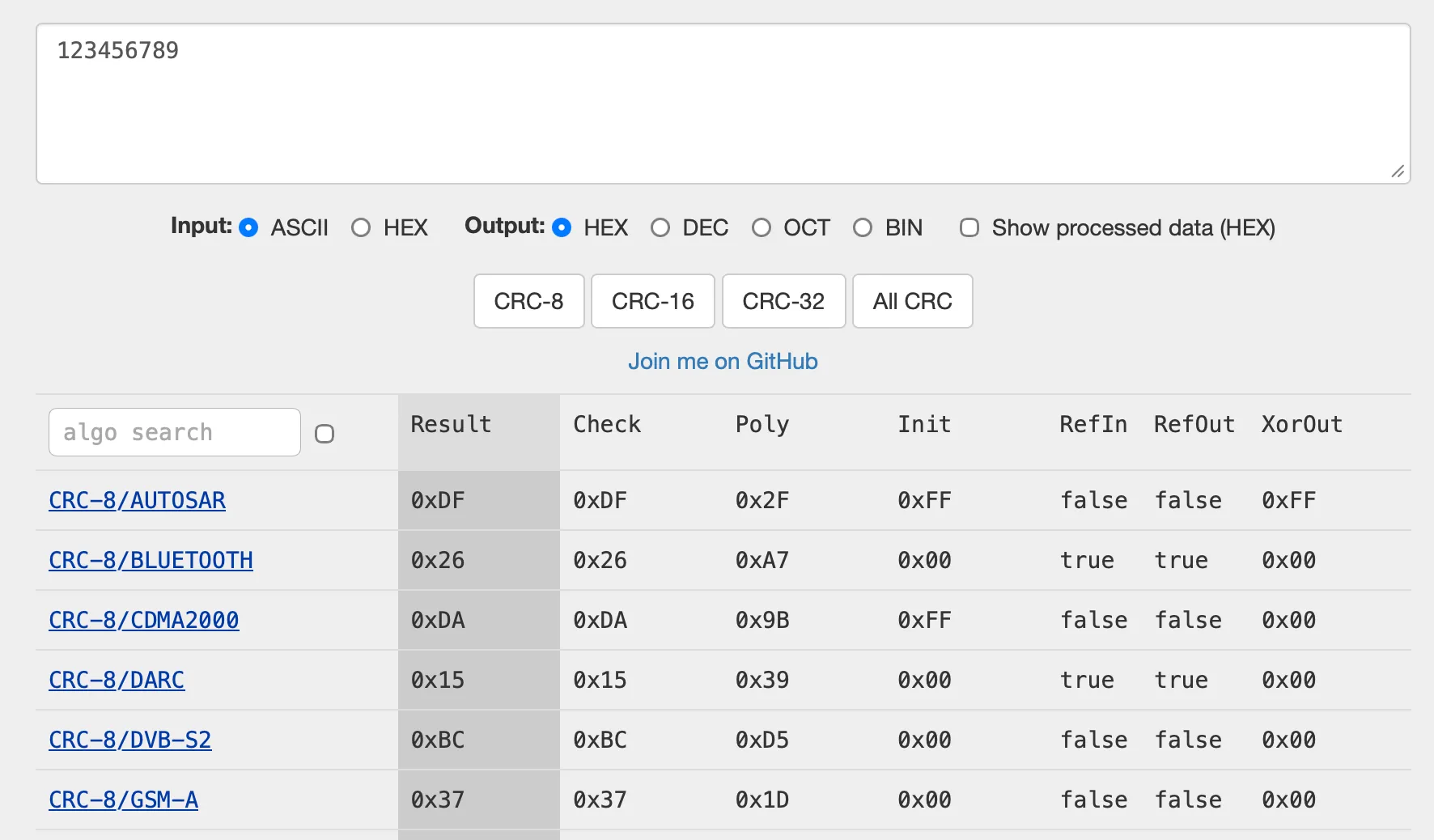
You can use crccalc.com to test CRC16 variants with a known packet.
You can experiment with settings like bit reflection, polynomial, or initial value. crccalc updates in real time, making trial-and-error much faster.
Real-World Example
On a recent project, we were tasked with understanding the communication protocol with an old vending machine. The good thing was that there was documentation detailing the communication protocol. The bad thing was that the company no longer existed. Most of the documentation was quite detailed. However, the only thing mentioned about the checksum was “CRC16”. Our first three implementations didn’t match the device’s checksum.
Ah, thanks.
Luckily, there was a way to get the first message from the device, without requiring any CRC on our end. By pasting the frame into crccalc.com and testing variants, we quickly discovered it was CRC16-ARC, big-endian. Once identified, we verified it in code, and communication worked perfectly.
Connected! Or are we?
Why It Matters
This approach is essential when:
- Integrating with undocumented third-party devices
- Decoding proprietary protocols
- Migrating legacy systems where documentation is incomplete
A single captured packet is often enough to fully identify the CRC.

This one only knows Japanese
Final Thoughts
Reverse-engineering checksums doesn’t have to be trial and error. Tools like crccalc.com make it easy to explore CRC parameters interactively.
If you’re stuck with “CRC mismatch” errors or a vague CRC16 line in a datasheet, try this method—or reach out if you need help analyzing a tricky protocol.

Quick CRC analysis saves hours of debugging.
Need Help Solving CRC Issues?
If you’re dealing with undocumented protocols, CRC mismatches, or just need a quicker way to reverse-engineer checksums, we can help.
- We can analyze your captured packets and identify the correct CRC variant.
- We provide embedded software consulting for tricky hardware integrations.
- We offer guidance on implementing CRC checks reliably in your firmware.
📧 Contact us at altug@alsoft.nl
💼 Learn more about our Services